QUESTION
Writing briefly in :
The important of computer security and network security
1 The OSI (open systems interconnection) security architecture
2 the need for automated tools for protecting files and other information
3 the introduction of distributed systems and the use of networks and communications facilities for carrying data between terminal user and computer and between computer and computer
4 conventional algorithm definition
Writing in
cryptographic algorithms divided into three groups:
-
Symmetric
-
Asymmetric
-
Hash functions
Symmetric Algorithms(symmetric key cryptography)
-
Its mode (blockcipher ,streamcipher ,hash functions) in details.
-
In the block cipher please include (the structure of block cipher feistel cipher and spn ) Explain as much as you can .
symmetric key encryption techniques such as The DES Algorithm, Triple DES algorithm, the AES algorithm and Blowfish algorithm .Please (distribute this algorithm depend on there inner structure)
Asymmetric Algorithms 3 algorithm Explain( in details )
-
Diffie-Hellman (in general )
-
RSA in (General)
*Comparison Between Symmetric And Asymmetric Encryption
*PERFORMANCE FACTORS criteria for conventional algorithm
ANSWER
Solution
1
The OSI or Open Systems Interaction security architecture is a special framework which defines certain requirements and approaches for computer and network security. It focuses on three aspects which are Security attacks, Security mechanism, and Security services. [1]
-
Security attacks –
As per OSI architecture, there are two types of attacks. Active attacks alter the resources of a system or its operation. While passive attack learns the system or uses its information without affecting it.
-
Security Services –
Security services under OSI architecture are of following types:
-
Confidentiality – Information remains within authorised access.
-
Authentication – The authorisation is correct or not.
-
Integrity – Only authorised systems can change or share the information.
-
Non-repudiation – Neither a receiver nor the one who is sending can deny any information transmission.
-
Access control – Information can be controlled by the Target system.
-
Availability – The systems are available for authorised access.
-
Security Mechanisms –
OSI defines two types of security mechanisms: Specific and Pervasive. For Specific Security Mechanisms OSI focuses on –
-
Encipherment
-
Digital Signature
-
Access Control
-
Data Integrity
-
Authentication Exchange
-
Traffic Padding
-
Routing control
-
Notarization
For Pervasive Security Mechanisms, OSI isn’t specific but checks following :
-
Trusted Functionality
-
Security Label
-
Event Detection
-
Security Audit Trail
-
Security Recovery
2
Fir computer and network security, automated tools are required because of the following truths:
-
Uniform Strength
Automated tools can provide the ability and strength to fight any incoming attack, and hence can afford the highest level of protection.
-
High Efficiency
Automation streamlines the workflow, and the environment becomes more uniform and efficient. Hence security becomes stronger.
-
Fewer Errors
Cyber attacks in the past have generally come in the hands of overworked humans, and even skilled professionals can make mistakes. Automation eliminates any such error related problems.
-
Decision making
In case of any security breach, there can be situations to take decisions such as protection of specific data over others. This can be efficiently done through automated tools which by analysing data, prioritise them and make decisions. [2]
3
Distributed systems are recently being used along with Network and Communication facilities to carry data between computers and users. They are now used to enhance computer and network security. Since the information is distributed, every component can be assigned to a different security regime. Each domain with a different security regime can reflect a whole new policy which varies control to organisations. Following mechanisms are used for this:
-
Physical and electronic-based security
-
Authentication mechanism
-
Communication security
-
Access control mechanism
If such mechanisms are not implemented properly, then the distributed system can wreak havoc for data of both terminal user and other computers as hacking can be easier in such systems. [3] [4]
4
Conventional algorithms transform any plaintext into a ciphertext message which can be decrypted only by a key. The deciphering keys and enciphering keys are either identical or are derivable from each other. Due to this convention, both the keys must be secured. These are used extensively but are vulnerable to attacks owing to a number of keys which are available. The techniques used in this algorithm are –
-
Monoalphabetic
-
Polyalphabetic
-
Polygraphic
-
Route Transposition
-
Columnar Transposition
-
Synchronous Stream
-
Asynchronous Stream
-
Iterated Block
-
Fractional Block
-
Steganographic
1
Symmetric Algorithms are those cryptographic algorithms in which, for the purpose of decryption of ciphertext and encryption of plaintext, same cryptographic keys are used. [5] The encryption can be done in two modes:
-
Hash Functions – These are mathematical functions which can convert a numerical input to a new compressed numerical value. The output of the hash function is of fixed length, no matter what the input is. The hash function operations are relatively faster than general symmetric encryption.
-
Stream Cipher – In this mode, digits of plaintext are combined with a keystream of pseudorandom Cipher digits. Each plaintext digit corresponds to one digit of keystream at a time to give encrypted ciphertext.
-
Block Cipher – This is a little different. Here, multiple bits of plaintext is combined and then they are encrypted as a single unit. Here the plaintext is padded to make it a multiple of block size. The 64 bits block are common today.
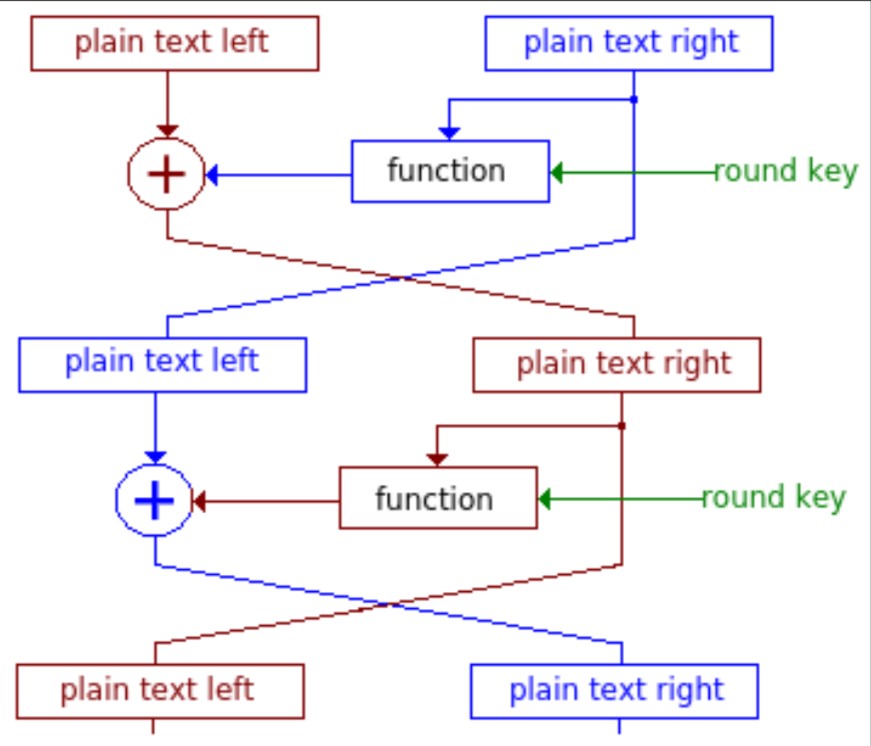
Feistel Cipher – In Block Cipher, Feistel Cipher design is generally used as its structure. Here, the algorithm remains the same for both encryption and decryption. In this, the bit on right half remains unchanged while the left bit goes to encryption and it depends on the right. It is done as shown in the following figure.
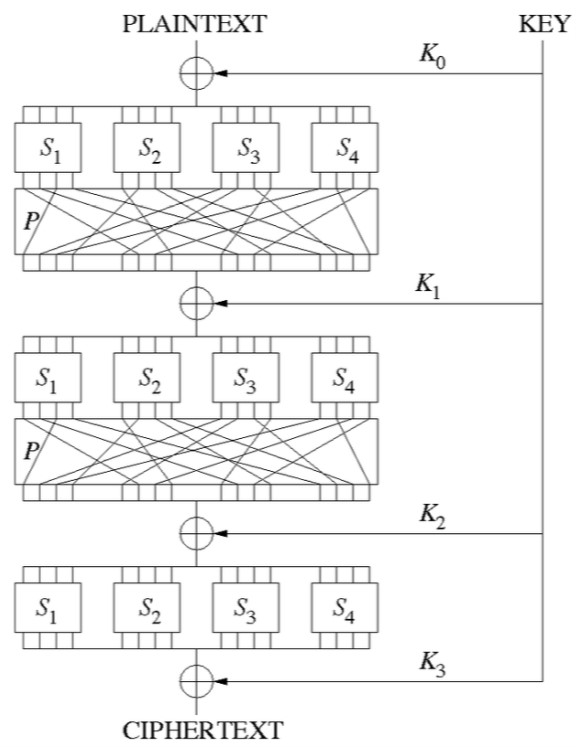
SPN – Substitution-Permutation Network is a mathematical operation series which are used in Block Cipher algorithms. SPN takes blocks of plaintext and encryption keys as inputs and applies alternating layers of permutation boxes and substitution boxes to create the ciphertext block. It is shown in this figure.
There are various symmetric encryption techniques such as The DES, Triple DES, AES and Blowfish algorithms. Each differs for the average bits they demand. DES demands 27 bits; Triple-DES demands 40 bits, AES wants 256 bits while the Blowfish algorithm demands 44 bits. [6][7]
2
Asymmetric Algorithms or public key cryptography corresponds to a cryptographic system which uses a public-private pair of keys. The public keys are available widely while private keys are with the owner only. These one-way function keys are generated using cryptographic algorithms based on mathematical problems. Every receiver has its own unique decryption key. Though the pair of keys is related mathematically, they can’t be recovered from each other. They are used to provide secrecy as in Diffie-Hellman system or provide digital signatures along with secrecy as in RSA system. [8]
-
Diffie-Hellman – This is a common method for exchanging cryptographic keys on a public channel. It provides a secret colour key to two parties, say, Alice and Bob. Each mixes their common message with that colour and then the encrypted message is sent to the public channel. Again the messages are mixed with the same secret colour and it becomes a common secret. If a third person tries to listen to this exchange, the common secret will be difficult to decode as secret colour keys will be impossible to decipher. The keys used are Colors rather than numbers as even the modern supercomputers can’t do that in a reasonable time.
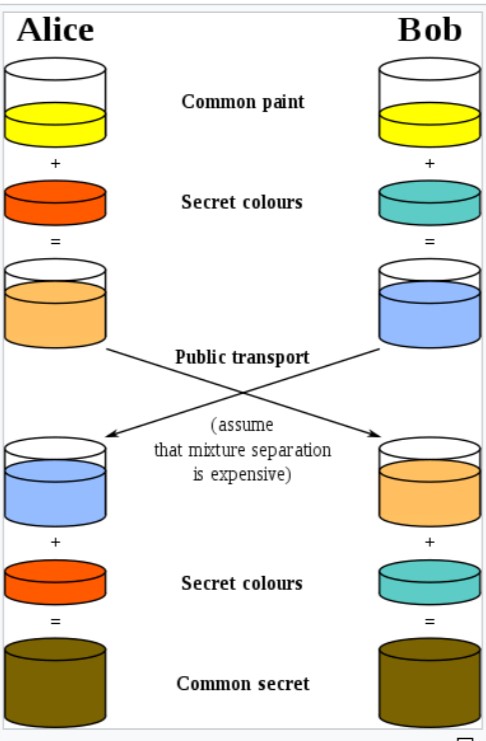
-
RSA cryptosystem – This is the basic system which provides both secrecy and digital signature and is widely used. In this, both the private and public keys can be used for encryption. If the public key is used for encryption, then the private key will decrypt it and vice versa. Its security is derived from the problem of factoring large integers, which are the product of a pair of large prime numbers. The factorisation is hard and so the security is better.
The symmetric and asymmetric algorithms vary on many points:
-
Symmetric uses only one encryption key but asymmetric uses two: public and private.
-
The asymmetric algorithm is rather complex than the symmetric one.
-
The asymmetric encryption process is a little bit slower than symmetric algorithms.
REFERENCES:
-
Tagarev, T., Sharkov, G., and Stoianov, N. (2017). Cyber Security and Resilience of Modern Societies: A Research Management Architecture.
-
Nizri, G. (May 3, 2016). Why automation is the key to the future of cybersecurity.
-
Ly, K., Sun, W., and Jin, Y. (2016). Emerging Challenges in Cyber-Physical Systems: A Balance of Performance, Correctness, and Security. University of Central Florida.
-
Elkabbany, G., and Rasslan, M. (August 2016). Security Issues in Distributed Computing System Models. Electronics Research Institute. Egypt.
-
Polk, W., Dodson, D., Burr, W., Ferraiolo, H., and Cooper, D. (May 2015). Cryptographic Key Sizes for Personal Identity Verification.
Looking for best Computer Science Assignment Help. Whatsapp us at +16469488918 or chat with our chat representative showing on lower right corner or order from here. You can also take help from our Live Assignment helper for any exam or live assignment related assistance.